Earlier last month, X became a target of a sophisticated DDoS attack causing outages across millions of users on the platform. This was not the only attack recorded for the month, there has been multiple attempts globally to control multiple platforms on the web.
ID spoofing, also referred to as identity spoofing, identity fraud, or impersonation attacks, is a malicious tactic where an individual or entity impersonates another person to deceive and manipulate others. This deceptive practice aims to gain unauthorized access to sensitive data, commit fraud, or engage in other illicit activities.
Understanding ID Spoofing
As AI advances, the sophistication of ID spoofing techniques has also increased. Fraudsters are now employing more advanced methods, like deep fakes and instant video AI avatars, to bypass security measures. For instance, fake identity fraud accounts for 80-85% of all identity fraud cases, with incidents rising significantly in recent years. This trend highlights the urgent need for robust security measures to protect both individuals and organizations from these evolving threats.
Techniques Used in ID Spoofing

- Biometric Manipulation: Fraudsters exploit biometric data, such as fingerprints or facial recognition, to impersonate legitimate users. They may use forged fingerprints or create realistic facial masks to deceive biometric authentication systems.
- Video Injection Attacks: This technique involves injecting fake videos and deep fakes into remote identity verification processes, allowing fraudsters to present themselves as legitimate users. Advanced detection systems are now being developed to identify and mitigate these threats. The increasing prevalence of deep fake technology undermines trust in online identity verification processes.
- Phishing and Social Engineering: Attackers often use deceptive emails, texts, or phone calls to trick individuals into revealing personal information, further facilitating identity spoofing. This erosion of trust can have far-reaching implications, particularly in the finance sector, where identity verification is critical for compliance and security.
How ID Spoofing Works?
There are three ways that ID spoofing works: first, by crafting spoofed packets where data packets of altered headers are created, mimicking a legitimate source. Another is by sending spoofed requests where the data packets are transmitted via the target’s network as a trusted source. Lastly, it is by exploiting trust. The targeted device processes the request as legitimate and allows the attacker to access data and execute commands.
IP address spoofing
IP address spoofing was the first known type of ID spoofing. This is done by creating data packets with modified source IP addresses that appear to be another device concealing the real origin of the attack, either by impersonating other users or bypassing network security protocols. One known incident was the GitHub DDoS Attack in 2018.
According to the information, attackers utilized IP address spoofing as part of a Memcached DDoS attack. They sent forged requests to vulnerable Memcached servers. The servers, thinking the requests were legitimate, responded with large amounts of data to GitHub’s spoofed IP address, overwhelming its systems. This brought down GitHub for 20 minutes.
Email Spoofing
Another one is email spoofing, which is almost a daily occurrence. In this type of attack, the sender’s email address is altered, making it appear that a legitimate company or trusted individual, such as a banking institution, sent it. These phishing attacks trick unsuspecting customers into providing sensitive information or downloading malware onto their devices. The Democratic National Committee (DNC) Hack in 2016 during the presidential elections is a perfect example.
According to the reports, hackers sent spear-phishing emails that appeared to be from Google, targeting DNC staff and tricking them into revealing their login credentials. The emails were crafted to look legitimate, using spoofed sender addresses and familiar language. Sensitive emails and documents were leaked, causing significant political turmoil and impacting the election cycle.
DNS Spoofing
DNS spoofing is another type in which the DNS data is corrupted to redirect users to malicious or fake websites where they are asked for sensitive information such as bank account details or login credentials. In 2012, several Brazilian banks were targeted by redirecting their online banking users to malicious websites that looked like the bank’s website. Many users had their banking information stolen, causing financial losses for the banks affected.
ARP Spoofing
Last is ARP spoofing. This involves linking the local area network to a MAC address with the IP address of a trusted device. It can block, modify, or stop the transmission of data on a local network, such as login credentials or any sensitive data. In 2003, a simulation was done called a Man-in-the-Middle Attack on ARP. A security researcher conducted an ARP spoofing on a local network. He was able to intercept and alter data packets between the network and the target device.
Consequences of ID Spoofing
The implications of ID spoofing are severe, leading to significant financial losses, security breaches, and a loss of trust in digital systems. Once an individual’s identity is compromised, recovery can be challenging, making prevention and detection critical.
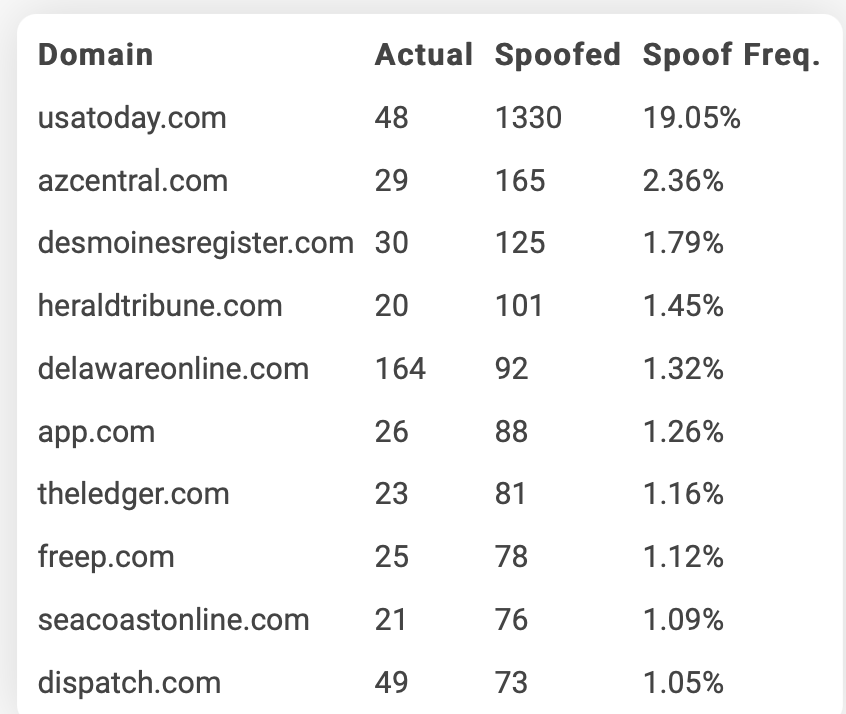
Online Ad Fraud
Another significant consequence of ID spoofing is its contribution to online ad fraud. Fraudsters can use spoofed identities to create fake accounts and generate false traffic, leading to inflated advertising costs for businesses. This manipulation can result in wasted marketing budgets, skewed analytics, and misallocated resources. In 2023, it was estimated that online ad fraud could cost businesses upwards of $100 billion annually, highlighting the critical need for effective detection and prevention strategies.
Challenges in Recovery
Recovering from ID spoofing incidents can be a complex and lengthy process. Victims often face difficulties in proving their identity, restoring their credit, and rectifying unauthorized transactions. The emotional toll of having one’s identity compromised can also lead to anxiety and stress, further complicating the recovery process.
Financial Losses and Security Breaches
ID spoofing can result in substantial financial losses for both individuals and organizations. Victims may face direct theft of funds, unauthorized transactions, and costs associated with identity recovery. Organizations can incur costs related to legal liabilities, regulatory fines, and damage to their reputation, leading to a decrease in customer trust and business opportunities.
According to recent reports, mobile users globally are expected to lose $58 billion to scam calls involving ID spoofing in 2023, a significant increase from the $53 billion lost in 2022.
Mitigating ID Spoofing Risks
To combat ID spoofing, organizations must implement comprehensive security strategies that include:
- Robust Biometric Systems: Utilizing advanced biometric authentication technologies that incorporate liveness detection can help ensure that the person presenting the biometric data is physically present.
- Continuous Monitoring: Regularly monitoring suspicious activities and employing advanced algorithms for real-time detection of spoofing attempts can significantly reduce risks.
- User Education: Educating users about the dangers of phishing and safeguarding personal information is essential in preventing identity spoofing.
- Advanced Detection Technologies: Utilizing machine learning and AI-based systems can help detect anomalies in calling patterns and identify potential spoofing attempts before they reach the consumer. These systems can analyze call metadata and flag suspicious activity for further investigation.
MonetizeMore’s Traffic Cop
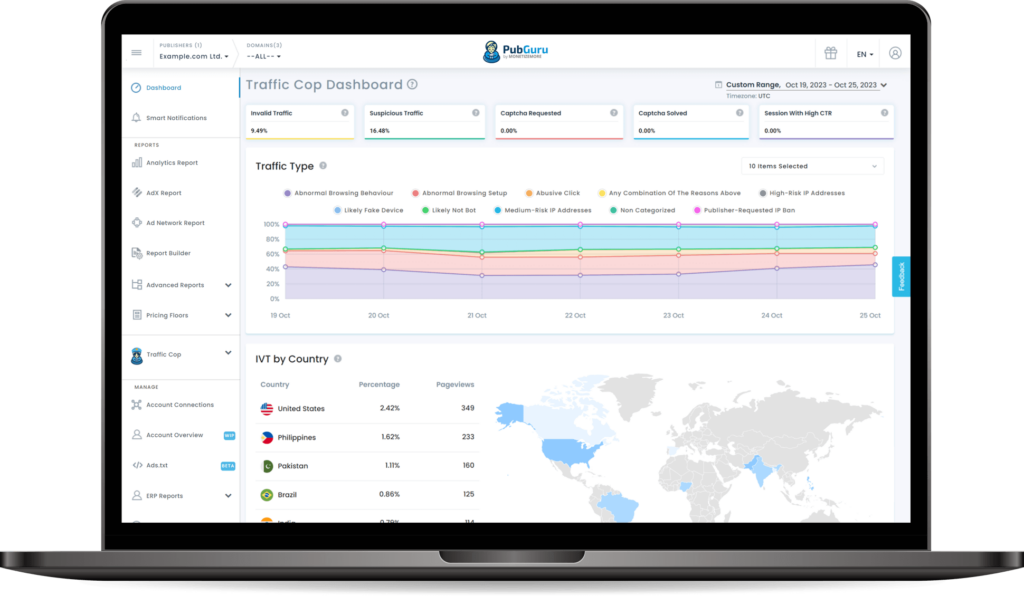
Traffic Cop is a robust solution to combat ID spoofing related to ad fraud. This tool employs advanced algorithms to analyze invalid traffic patterns and detect fraudulent activities, ensuring that stakeholders are not misled by fake clicks or impressions generated by spoofed identities. By identifying and filtering out illegitimate traffic, Traffic Cop improves the overall integrity of online ad campaigns.
Putting an end to ID Spoofing
Implementing powerful security protocols can mitigate or stop all these types of attacks. Organizations should execute network filtering, ingress/egress filtering, email authentication protocols, and anti-spoofing tools.
MonetizeMore’s Traffic Cop stands out as a solid solution for publishers looking to protect their ad revenue from ID spoofing and other forms of invalid traffic. By leveraging advanced detection techniques, real-time blocking capabilities, and detailed traffic analytics, Traffic Cop empowers publishers to maintain the integrity of their advertising ecosystems and optimize their monetization strategies. Try Traffic Cop here!
source https://www.monetizemore.com/blog/id-spoofing/


0 Comments